
Ok, so you might have noticed in the recent couple of weeks, the dreaded XZ utils backdoor vulnerability where many companies are stressing that the vulnerability might effect them.
What is XZ Utils Backdoor?
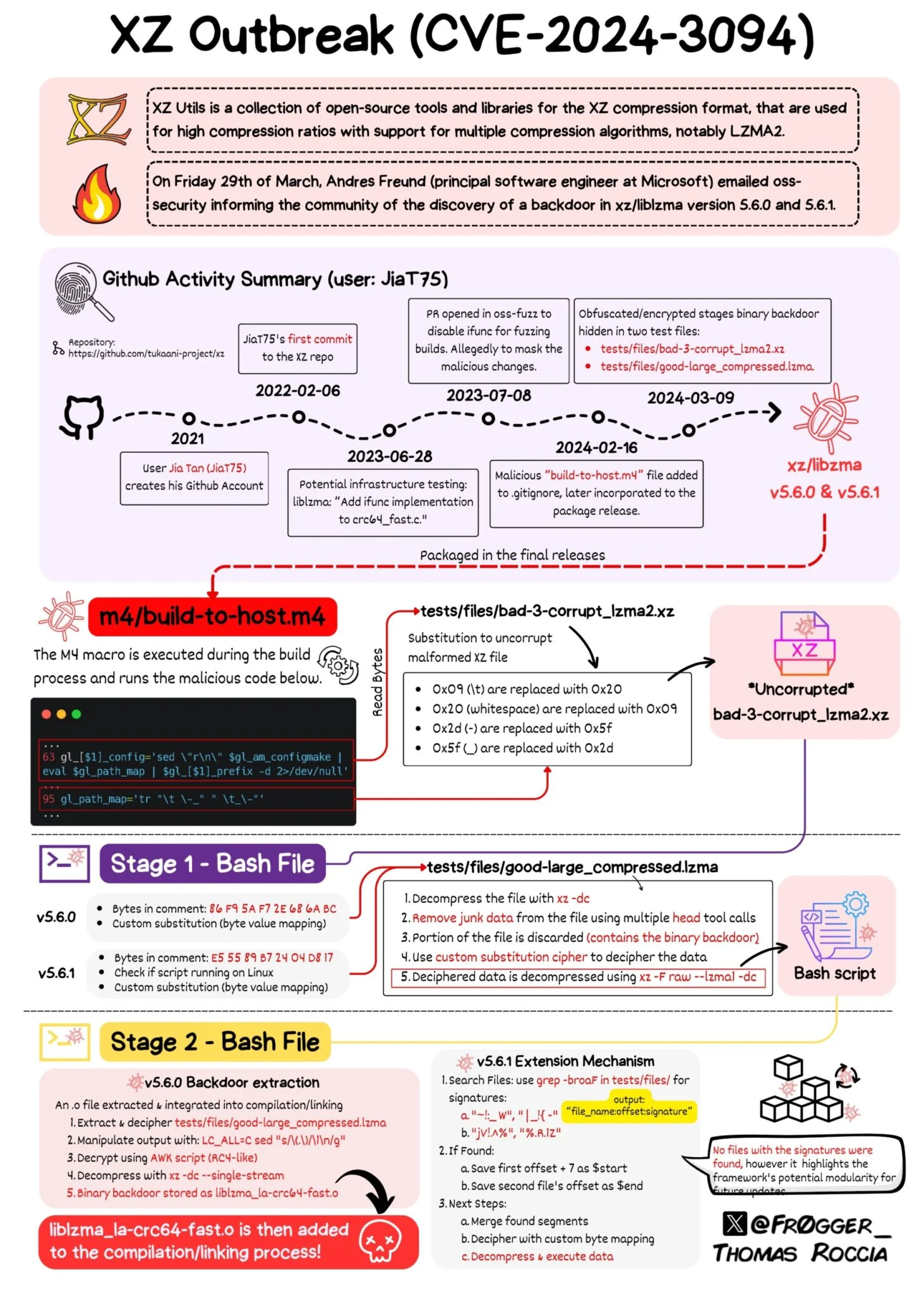
First, let’s dive into what the XZ utils backdoor vulnerability actually is. XZ utils are widely used for data compression and decompression across various systems, including Linux distributions. The vulnerability stems from a backdoor that could potentially allow unauthorized access to systems, leading to data breaches or other malicious activities.
However, I’m not concerned and here’s why:
Leveraging Tailscale VPN for Enhanced Security
My new found love (in the computer world) (not sponsored):

The primary reason I am not worried is because I leverage tools like Tailscale VPN. Tailscale VPN offers a unique advantage by facilitating secure access to my servers regardless of their physical location. This means that even if my servers are spread across different networks or regions, I can seamlessly connect to them as if they were on the same local network.
One of the standout features of Tailscale VPN is its ability to access ports securely. Traditionally, exposing ports to the internet can pose significant security risks, as they become potential entry points for attackers. However, with Tailscale VPN, I can securely access specific ports on my servers without exposing them to the broader internet. This granular control ensures that only authorized users can interact with designated services, reducing the attack surface and bolstering overall security.
Robust Patching and Updates
Another reason I’m not losing sleep over this vulnerability is the swift response and availability of patches. The open-source community and other stakeholders typically respond quickly to such threats, providing patches or updates to mitigate risks. I maintain a disciplined approach to applying these updates, which should shield me from potential exploits.
Blocking Port 22 Inbound on Servers
As part of my multi-layered security approach, another effective strategy I employ is blocking inbound connections on Port 22 on all my servers. Port 22 is commonly used for SSH (Secure Shell) connections, which are essential for remote server management. While SSH is a powerful tool for administrators, it also represents a common vector for attacks, particularly brute force attempts.
By blocking inbound connections on Port 22, I significantly reduce the risk of unauthorized access. Instead of leaving this port open to the internet, I utilize tools like Tailscale VPN to establish a secure and controlled environment for accessing my servers. This setup allows me to manage my servers remotely without exposing the SSH service directly to the internet, thereby minimizing potential attack surfaces.
This practice aligns perfectly with the use of Tailscale VPN, as mentioned earlier. Tailscale enables secure, encrypted tunnels for accessing ports safely, so there’s no need to expose Port 22 directly to the internet. This way, I maintain the functionality required for efficient system administration while significantly enhancing my security posture.
Here’s a quick and easy guide to better protect yourself:
xz --version on your terminal to identify the version of XZ Utils installed.iptables or ufw to manage firewall settings./etc/ssh/sshd_config) and set PermitRootLogin no.PasswordAuthentication no in the SSH configuration file.sudo systemctl restart sshd).It is important to keep a server updated with the latest critical security patches and updates. Otherwise you’re at risk of known security vulnerabilities that bad-actors could use to gain unauthorized access to your server.
Unless you plan on checking your server every day, you’ll want a way to automatically update the system and/or get emails about available updates.
You don’t want to do all updates because with every update there is a risk of something breaking. It is important to do the critical updates but everything else can wait until you have time to do it manually.

